SaaS Governance - A Critical Industry Need
A critical industry need that shows no signs of slowing down!
It’s now been nearly two years since I initially authored an article titled, “Why You Need a SaaS Governance Plan, and What Should Be In It,” on CSO Online. In the article I discussed how the rapid proliferation of SaaS applications and consumption by organizations represented a significant business risk and how SaaS Governance can help mitigate that risk.
The topic struck a nerve with the industry and I was able to subsequently lead a Cloud Security Alliance (CSA) Working Group to publish the “SaaS Governance Best Practices for Cloud Customers” whitepaper in October 2022, which is the most comprehensive and vendor-agnostic SaaS governance and security publication in the industry to my knowledge.
While SaaS adoption was already seeing tremendous growth, the introduction of the COVID pandemic and exponential increase in the adoption of remote work only accelerated SaaS use. As I mentioned in my original article in 2021, the conversation around cloud security within the industry traditionally has been incredibly IaaS-centric.
This makes sense on the surface when we consider the size of leading IaaS cloud service providers (CSPs) such as Amazon Web Services (AWS), Google Cloud, and Microsoft Azure. However, while organizations are using on average two to three IaaS providers, they are using literally hundreds of SaaS providers and applications, especially in large complex enterprise environments. Studies I cited at the time showed that SMB’s were using over 100 SaaS applications, while large enterprises were using nearly 300 different SaaS applications.
Despite this overwhelming presence of SaaS usage, industry-wide and organizationally, nearly all of our cloud security focus and activities revolve around securing IaaS. This is increasingly coming at our own peril as well, as we see a surge in software supply chain attacks reaching over 742% increases in the last 3 years, per sources such as Sonatype. Included in those figures is software delivered as-a-service, particularly SaaS, as organizations increasingly consume their software and applications from third-party providers. We saw this manifest in situations such as the Twilio security incident, which subsequently went on to impact over 130 other organizations. Malicious actors increasingly see the software supply chain as a brittle and enticing attack surface where they can have a cascading downstream impact on software consumers, and this applies just as much software delivered as-a-service, such as SaaS.
Thankfully, organizations and security leaders are waking up to the dangers of ungoverned and insecure SaaS usage and we are seeing growing interest in making use of tools such as SaaS Security Posture Management (SSPM) as well as investing resources and time in SaaS governance and security organizationally.
As I originally discussed in 2021, while cloud security is a broad domain, SaaS has some specific risks that make it unique and challenging in its own right. We know that on average less than 30% of SaaS usage is controlled directly by organizations’ IT/security teams, and often, these teams are totally oblivious to the extent of their organization’s SaaS consumption, what data resides in the SaaS providers’ environments, who has access to it, or the complex interdependencies that present risk to their organization due to SaaS integrations and utilizing SaaS as part of their core business processes and workflows.
Other complicating factors include the reality that unlike a major IaaS platform that has a standardized set of features, configurations, and capabilities, SaaS providers vary immensely and that variation is exponential due to the hundreds of SaaS applications being used in the modern organization. It is simply unrealistic and impractical to expect someone to possibly know and understand how to secure hundreds of different SaaS applications and their unique configurations and features without the use of automation and innovative SaaS security tooling.
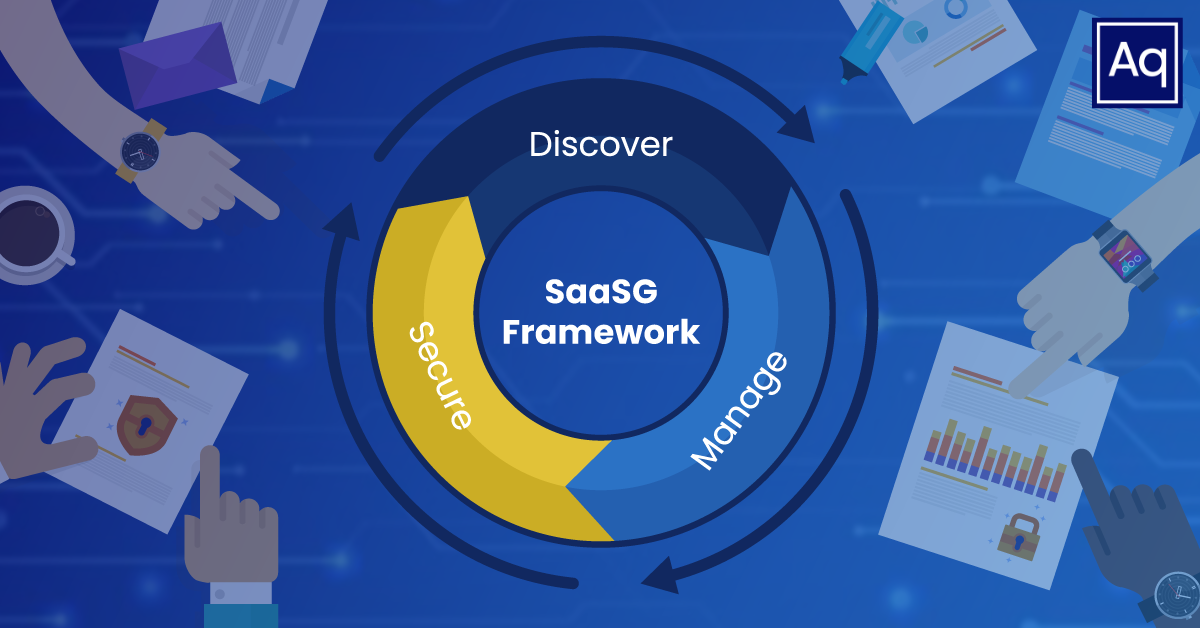
Thankfully, since 2021, my team at Aquia Inc. has had a chance to develop experience in the unique area of SaaS governance and security by establishing and leading a SaaS Governance team in a large, complex federal agency. This program has been oriented around three key pillars, which include the activities of “Discover, Manage, and Secure.” That is discovering what SaaS is in use, establishing flexible but sufficient processes to manage the assessment and sanctioning of new SaaS applications, and ultimately securing the known SaaS footprint.
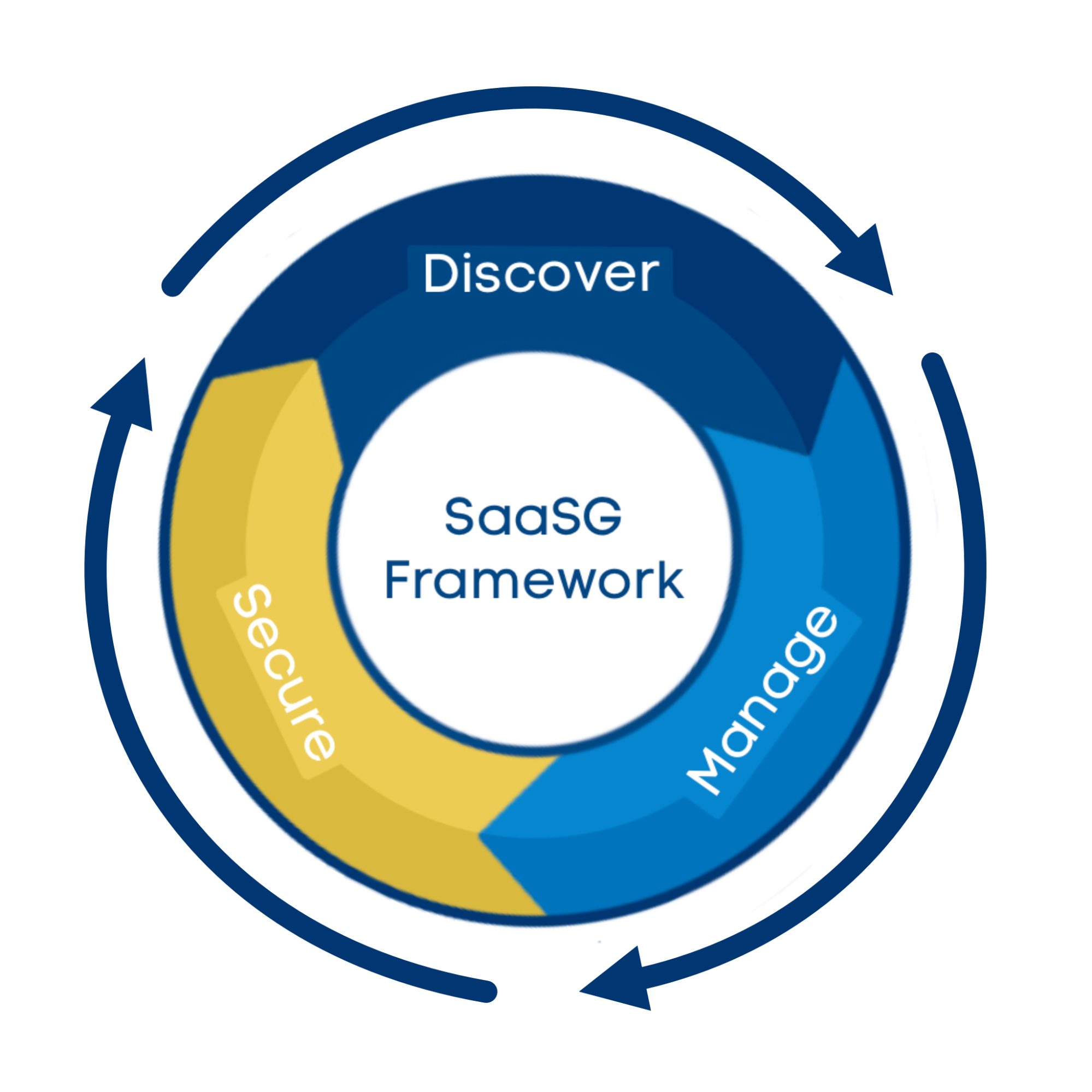
As discussed by an agency leader in a recent interview, this program and activity has involved facilitating a largely distributed and remote workforce, working around current limitations of existing compliance requirements and processes, as well as leveraging innovating cloud-native technologies and capabilities to both discover and secure the agency’s usage of SaaS while not negatively impacting the business owners, staff, or mission, which is a challenging endeavor. All of these activities are occurring as part of a broader SaaS Governance program to help the agency continue to adopt cloud and SaaS as part of enabling their mission but doing so in a manner that mitigates risks to both the agency and the stakeholders they serve.
Part of that process has included working with cloud-security leader, Axonius, who has provided desperately needed capabilities in terms of asset discovery, including SaaS usage as well as SaaS security and hardening to mitigate the risk of known SaaS usage by the agency.
Tools such as these are key to enabling secure SaaS consumption while not impeding the organization from utilizing the myriad of benefits that cloud adoption, including SaaS provide. Software will continue to be a focus for malicious actors and SaaS represents a core component of the software supply chain with a heavily concentrated customer/user base, and organizations failing to account for SaaS in their cloud security strategy and overall cybersecurity and risk management programs are leaving themselves open for potentially critical impacts and consequences.
Chris will be speaking on the topic of “Securing SaaS Applications” at Adapt 2023 on April 13 in Washington, D.C. You can learn more and register for the event here.
If you have any questions, or would like to discuss this topic in more detail, feel free to contact us and we would be happy to schedule some time to chat about how Aquia can help you and your organization.

