When Zero Trust Makes Zero Sense
Exploring what this buzzword means and how it can lay the foundation for a more effective security practice when approached correctly
Seemingly everywhere you turn today, vendors tout their products as the silver bullet for implementing Zero Trust, yet the actual concept remains elusive amidst the noise. When you read the product description, it might cover a single pillar of Zero Trust or simply be related to security with the Zero Trust label thrown on. So, what exactly is Zero Trust, and why is it hailed as, “the next big thing”? Amidst the clamor, Zero Trust often seems to make zero sense. In this post, we’ll break down what the framework actually is and why you can’t achieve it by simply incorporating one or two security products.
Defining Zero Trust
According to various industry bodies like the Cloud Security Alliance (CSA), the General Services Administration (GSA), and the Cybersecurity and Infrastructure Security Agency (CISA), Zero Trust is defined through different frameworks. For this discussion, we’ll focus on CISA’s model, which comprises five pillars: Identities, Devices, Networks, Applications & Workloads, and Data, with three foundational principles (Visibility and Analytics, Automation and Orchestration, and Governance.)
At its core, Zero Trust is identity-centric, but does not solely rely on verified identities. Instead, it embraces principles like least privilege, micro-segmentation, encryption, and other techniques to mitigate the impact of potential compromises — a concept that aligns with the overarching principle of “assume breach.” Essentially, Zero Trust represents a paradigm shift — a mindset — rather than a mere collection of tools or procedures.
The Old School Approach to Network Security
Traditionally, traffic that is inside the security boundary was implicitly trusted. Authentication did still occur for some resources, such as not being able to access the file server until authenticated. But malicious traffic could flow across a network while performing malicious actions such as scanning ports, sending malformed packets, Denial Of Service (DOS) and Distributed Denial Of Service (DDOS) attacks, payload attacks, and other malicious traffic. Security tooling was developed to detect and mitigate these types of attacks, but ultimately traffic was trusted once inside a security boundary. (Think: the castle and moat analogy, which my colleague Mack Wartenberger does a nice job explaining in this brief video.)
How is Zero Trust Different?
Zero Trust turns the old school approach on its head by demanding that traffic be authenticated before flowing. Technologies such as 802.1x and Network Access Control (NAC) were developed and can be used as part of a comprehensive Zero Trust solution, but they are not the entire answer (you will often see these products advertised as “Zero Trust,” but as we all now know, they are not Zero Trust, only a possible tool to support a holistic Zero Trust strategy). A holistic strategy must address the fundamental tenets.
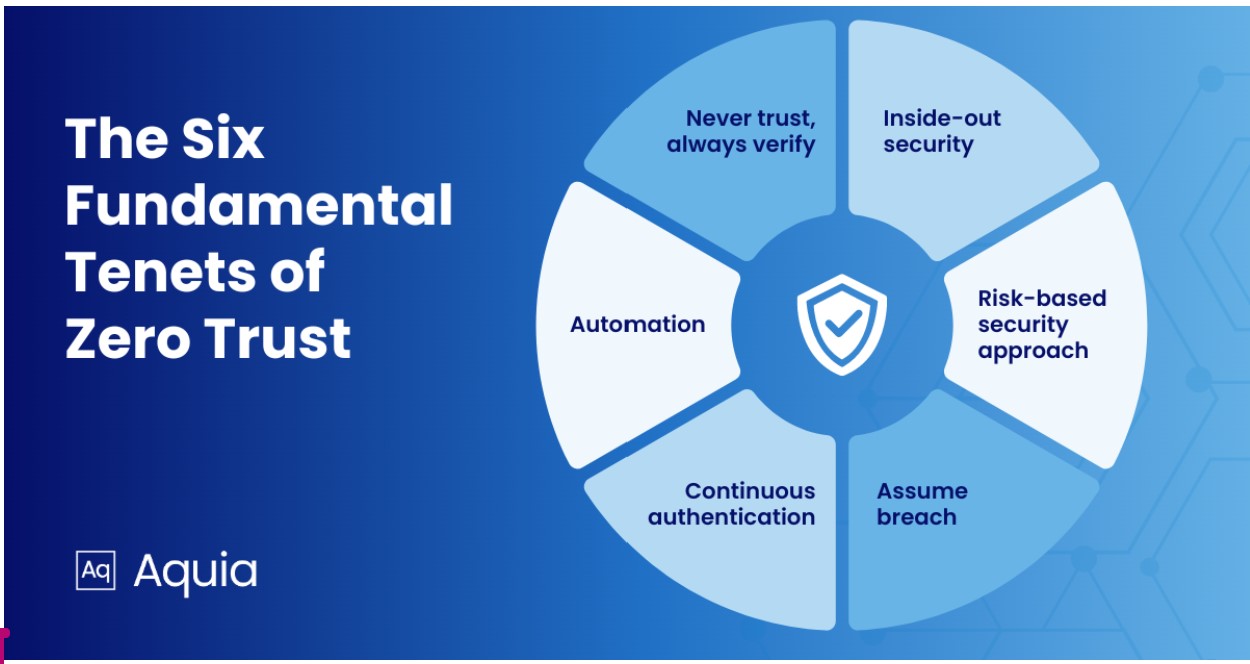
When we delve into Zero Trust’s design principles, we reveals its fundamental tenets: never trust, always verify; inside-out security; risk-based security approach; assume breach; continuous authentication; and automation.
Never trust, always verify ensures that requests to assets are never implicitly trusted, as they were in the past. Network traffic, API calls, Non-Person Entity (NPE) requests, and all other transactions must be verified to be legitimate before being allowed on the network or processed. This requires continuous verification of the user’s identity, device security posture, and the context of the request before granting access to resources. Threats can be both external and internal and we must understand that any user or device, whether inside or outside the network perimeter, could be compromised. Therefore, access to resources are granted on a least-privileged basis and only after thorough authentication and authorization checks.
Inside-out security prioritizes safeguarding the most critical assets based on their value and vulnerability. Unlike relying solely on products, this approach demands a nuanced understanding of an organization’s unique environment and its “crown jewels” — elements requiring utmost protection. For example, Amazon Web Services (AWS) requires that the servers be online and accessible, so they will protect the infrastructure and internet access as part of their core business.
Risk-based security is based on understanding the risks that an organization faces and how to best prioritize a limited budget with a limited amount of manpower. All organizations are faced with limited resources and must deploy them judiciously. For example, placing authentication mechanisms around public information consumes resources that could be better deployed to protect more valuable assets. Protection decisions, as with inside-out security, must be based on the asset’s business value.
Assume breach instills a proactive security mindset, acknowledging the possibility of hostile actors within the system. By assuming that a hostile actor is already in the system, organizations are compelled to enforce measures like least privilege, micro-segmentation, and continuous authentication, bolstering internal security practices.
Continuous authentication utilizes multifaceted authentication methods, including context-aware authentication, considering contextual factors such as location, device status, and time of day. Unlike traditional authentication, access is continuously evaluated based on evolving factors, ensuring heightened security instead of authentication being “grant and forget.” Actions that the user takes, any changes in network traffic, and other data points are considered, and access can be revoked if enough changes occur or new information emerges during the session.
Automation plays a pivotal role in Zero Trust by alleviating “alert fatigue” and expediting response times. By automating detection and response processes, organizations can swiftly address security incidents, minimizing the impact of potential breaches. For example, you do not want to know that there is a breach and take hours to revoke access. By utilizing automation, response to threats may be reduced to minutes or even seconds. In today’s high-speed world, that could be a difference between a massive data breach and a limited scope incident.
There’s No Silver Bullet to “Achieving” Zero Trust
In essence, while addressing individual pillars of Zero Trust may offer incremental improvements, true comprehension necessitates embracing the Zero Trust mindset and the fundamental tenets holistically. Only when viewed as a cohesive framework do the complexities of Zero Trust crystallize into a comprehensive strategy — a monumental leap forward in fortifying organizational security. No longer does Zero Trust make zero sense, but it is the foundation for an effective security practice.
Eric Jackson is a principal security architect at Aquia. He has supported commercial and government customers in their transition to Zero Trust. Eric Jackson | LinkedIn
Your organization’s journey to robust Zero Trust doesn’t have to be an impossible mission, let Aquia’s expertise in Zero Trust Architecture (ZTA) guide you in fortifying your organization’s approach to Zero Trust architecture and overall cybersecurity posture. We can help you navigate the Zero Trust journey and achieve a more secure future.
Interested in learning more about what zero trust is (and isn’t)? Join us for our LinkedIn Live, “Unraveling the Complexities of Zero Trust: Why It’s Not a Product You Can Buy” on June 20 at 12 p.m. ET. Register here.
If you have any questions, or would like to discuss this topic in more detail, feel free to contact us and we would be happy to schedule some time to chat about how Aquia can help you and your organization.

